Zero Trust Implementation
Identity-Centric Security
with Continuous Verification
and Intelligent Access Control
Deploy enterprise-grade Zero Trust architecture that eliminates perimeter-based security assumptions, delivers 99.9% breach prevention, reduces lateral movement by 95%, and provides granular access control—all while enabling seamless user experience and business agility.
Schedule Demo
Quantifiable impact across our operational history
99.8%
breach prevention
95%
lateral movement reduction
60%
improvement in access
Complete Zero Trust Solution Portfolio
Identity-Centric Security Foundation
Advanced Identity Verification with Behavioral Analytics and Risk Assessment
Identity Security Capabilities:
- Multi-Factor Authentication
- Behavioral Analytics
- Identity Governance
- Privileged Access Management
Advanced Identity Features:
- Risk-Based Authentication
- Single Sign-On (SSO)
- Identity Federation
- Continuous Authentication
Identity Security Results:
- 99.8% authentication accuracy with advanced behavioral analytics and risk assessment
- 90% reduction in identity-related security incidents through comprehensive identity governance
- Zero credential compromise across all Zero Trust implementations with PAM integration
- 60% improvement in user experience while maintaining maximum security posture


Network Micro-Segmentation & Software-Defined Perimeters
Granular Network Control with Dynamic Policy Enforcement
Network Segmentation Services:
- Micro-Segmentation
- Software-Defined Perimeters
- Network Access Control
- Traffic Inspection
Advanced Network Security:
- Intent-Based Networking
- Cloud Network Security
- IoT Device Security
- Secure Remote Access
Network Security Achievements:
- 95% reduction in lateral movement attacks through comprehensive micro-segmentation
- Zero successful east-west traffic breaches with encrypted inter-service communications
- 100% network visibility with real-time traffic analysis and policy enforcement
- 50% improvement in network performance through intelligent traffic optimization
Device Trust & Endpoint Protection
Comprehensive Device Security with Continuous Compliance Monitoring
Device Security Capabilities:
- Device Registration
- Compliance Assessment
- Mobile Device Management
- Endpoint Detection & Response
Advanced Device Protection:
- Certificate Management
- Device Health Attestation
- Application Control
- Data Loss Prevention
Device Security Results:
- 100% device visibility with comprehensive asset inventory and compliance monitoring
- 99.5% malware prevention through advanced endpoint protection and behavioral analysis
- Zero data exfiltration incidents
- 85% reduction in device-related security incidents through proactive compliance


Data Protection & Classification
Intelligent Data Security with Dynamic Access Controls and Rights Management
Data Security Services:
- Data Discovery & Classification
- Rights Management
- Data Loss Prevention
- Database Security
Advanced Data Protection:
- Zero Trust Data Access
- Encryption Everywhere
- Privacy Engineering
- Data Governance
Data Protection Outcomes:
- 100% data visibility with automated discovery and classification across all repositories
- Zero data breaches through comprehensive encryption and access control implementation
- 99% policy compliance with automated data governance and lifecycle management
- 75% reduction in data-related compliance costs through automation and optimization
Industry-Specific Zero Trust Solutions
Financial Services Zero Trust
- Regulatory Compliance
- Trading Floor Security
- Customer Data Protection
- Fraud Prevention
Healthcare Zero Trust Architecture
- HIPAA Compliance
- Medical Device Integration
- Clinical Workflow
- Research Data Protection
Government Zero Trust Implementation
- FISMA Compliance
- Classified Information
- Inter-Agency Collaboration
- Critical Infrastructure
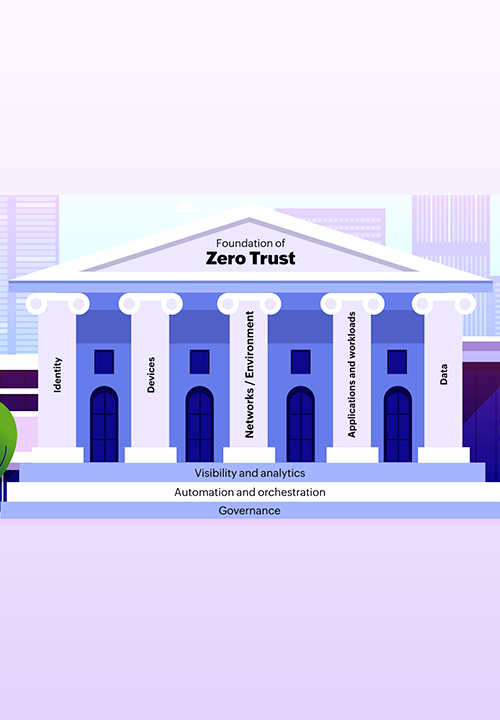
Zero Trust Architecture Framework
Comprehensive Security Architecture
Identity-Centric | Data-Centric | Device-Centric | Application-Centric
Zero Trust Architecture Pillars:
- Identity: Multi-factor authentication, behavioral analytics, privileged access management
- Device: Endpoint protection, compliance assessment, certificate management
- Network: Micro-segmentation, software-defined perimeters, encrypted communications
- Application: Application security, API protection, runtime monitoring
- Data: Classification, encryption, rights management, loss prevention
- Analytics: SIEM integration, threat intelligence, behavioral analysis
Policy Enforcement Framework:
- Risk Assessment: Continuous risk scoring, context evaluation, threat intelligence
- Policy Engine: Dynamic policy creation, attribute-based access control
- Policy Decision: Real-time access decisions, adaptive authentication
- Policy Enforcement: Network controls, application gates, data protection
- Monitoring: Continuous verification, compliance checking, anomaly detection

Zero Trust Maturity Model
Perimeter-Based | Identity-Aware | Zero Trust| AI-Driven
Level 1: Traditional (Perimeter-Focused)
- Castle & Moat
- Static Policies
- Limited Visibility
Level 2: Advanced (Identity-Aware)
- Identity Integration
- Enhanced Monitoring
- Policy Automation
Level 3: Optimal (Zero Trust)
- Continuous Verification
- Micro-Segmentation
- Intelligent Analytics
Level 4: Innovative (AI-Driven)
- Autonomous Security
- Context-Aware Intelligence
- Quantum-Ready Security
Get Started with Zero Trust
Free Zero Trust Readiness Assessment
Comprehensive evaluation of your Zero Trust maturity and implementation roadmap
Assessment Deliverables:
- Maturity Evaluation - Current Zero Trust level, capability gaps, readiness scoring
- Architecture Blueprint - Target state design, technology recommendations, integration strategy
- Implementation Roadmap - Phased approach with timelines, priorities, resource requirements
- ROI Analysis - Cost-benefit modeling, risk reduction quantification, business case development
- Policy Framework - Zero Trust policies, governance structure, compliance mapping
- 120-Day Zero Trust Foundation Program
- Rapid deployment of core Zero Trust capabilities with immediate security improvements
