
How To Build A Realistic Cyber security Plan For Third-Party Vendors (Infographic)
For any business to sustain and develop, vendor management is necessary and so is the security of those vendors for, they are the most vulnerable parties for security breaching. It is highly impractical to monitor each vendor as there are many factors involved to be taken care of. Despite the barriers, we face how do we ensure that your valuable information is not being eavesdropped?
To remain secure, these resource-intensive and time-consuming processes must be supplemented with a more scalable solution. Here we provide you step by step approach to building a realistic vendor cybersecurity plan.
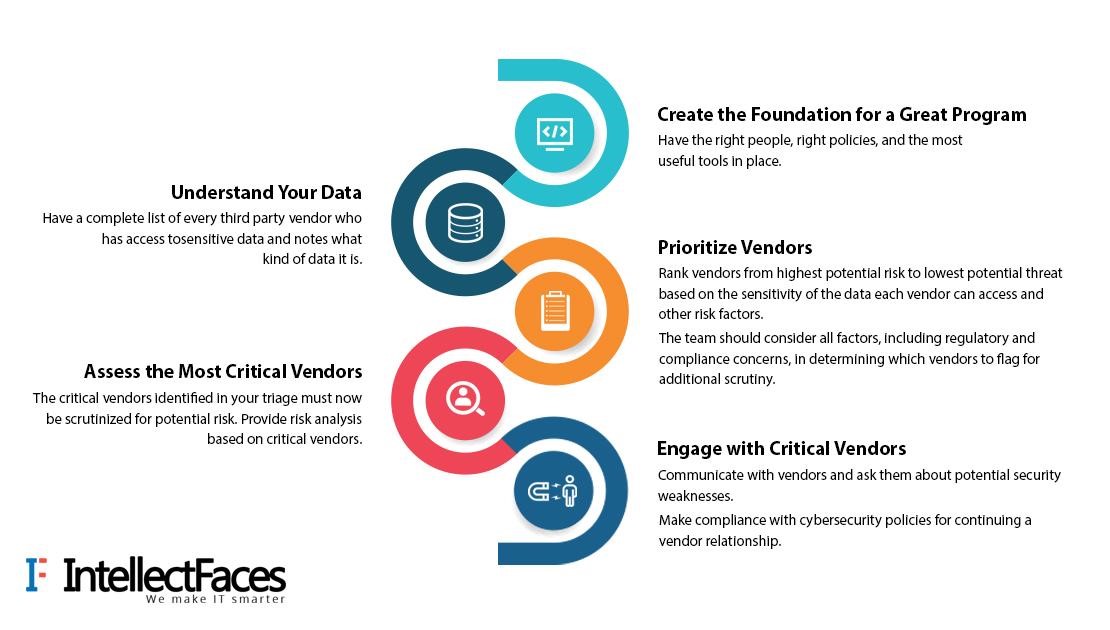
Concerning the ancient saying, “Power of information lay in the hands of the people who know it,” the above-stated ways eliminate the risk of your information leaking outside.
